
Encryption Made Easy: How to Secure Your Files Like a Pro
Introduction
From personal photos to business-critical documents, modern life relies on massive amounts of digital data. But every time we upload, email, or store data online, it can be exposed to unauthorized access. Encryption is one of the most reliable methods to keep information private and protected. This beginner-friendly guide explains what encryption is, why it matters, and how to use it to secure files and communications.
What Is Encryption?
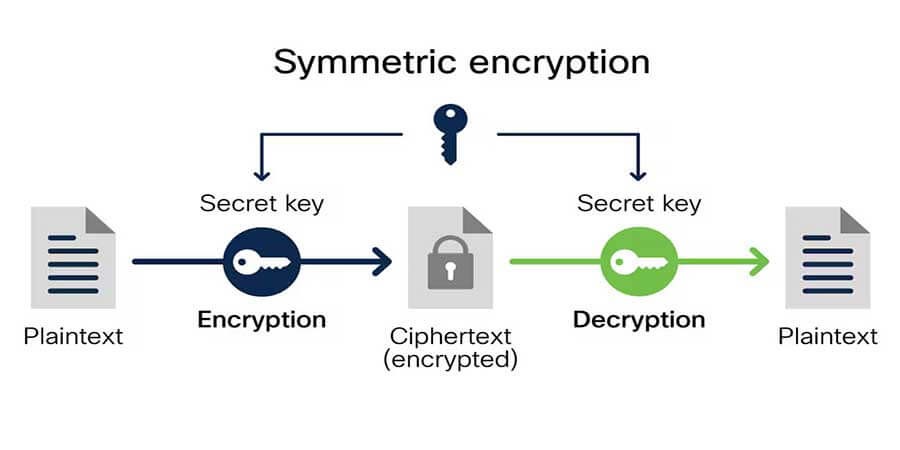
Encryption is the process of converting readable data (plaintext) into unreadable data (ciphertext) using an algorithm and a key. Only those with the decryption key can revert the data to its original form.
Key Terms:
-
Plaintext: Readable data
-
Ciphertext: Encrypted data
-
Key: Code used to encrypt/decrypt
-
Algorithm: The method used to scramble the data
Example: When shopping online, your credit card number is encrypted before being sent. Without the key, an intercepted file is meaningless.
Why Encryption Is Important
-
Privacy Protection: Prevents third parties from reading your emails or documents
-
Data Security: Ensures sensitive files (e.g., financial info) remain confidential
-
Regulatory Compliance: Required by laws like GDPR, HIPAA, and PCI-DSS
-
Cloud Trust: Encryption ensures even service providers can’t read your files
Symmetric vs. Asymmetric Encryption
Symmetric:
-
Same key used to encrypt and decrypt
-
Example: AES
-
Fast but key-sharing is risky
Asymmetric:
-
Public key to encrypt, private key to decrypt
-
Example: RSA, ECC
-
More secure key exchange
Encryption in Daily Life
-
Messaging Apps: Signal, WhatsApp use end-to-end encryption
-
Websites: HTTPS uses TLS encryption
-
VPNs: Encrypt all internet traffic
-
Cloud Storage: Providers like Tresorit and Sync.com use zero-knowledge encryption
Popular Encryption Algorithms
-
AES-256: Symmetric, highly secure and fast
-
RSA: Asymmetric, ideal for small secure transfers
-
ECC: Modern alternative to RSA with better performance
-
ChaCha20: Lightweight, secure, great for mobile devices
Beginner-Friendly Encryption Tools
-
BitLocker (Windows): Full-disk encryption
-
FileVault (macOS): Native Apple encryption
-
VeraCrypt: Cross-platform tool for encrypted drives or containers
-
7-Zip/WinRAR: Create encrypted archives
-
Cryptomator/Boxcryptor: Encrypt files before cloud upload
Managing Keys and Passwords
-
Use strong, unique passwords
-
Store passwords in a manager like Bitwarden or KeePass
-
Backup recovery keys in secure offline locations
-
Use Multi-Factor Authentication (MFA)
Encryption for Emails and Messages
-
PGP/GPG: Encrypt and sign emails
-
Secure Messaging Apps: Signal, Telegram (secret chat), WhatsApp
Cloud Storage Encryption Tips
-
Use services with client-side encryption
-
Avoid storing sensitive data in plaintext
-
Use encrypted folders or containers
Mobile Device Encryption
-
iOS and Android support full-device encryption
-
Set strong passcodes
-
Enable remote wipe features
-
Use encrypted apps and password managers
Ransomware Awareness
-
Ransomware uses encryption to lock your files
-
Backup data offline or in the cloud
-
Keep security software updated
-
Don’t open unknown email attachments
The Future of Encryption
-
Quantum-Resistant Encryption: Needed to protect against future quantum computers
-
Homomorphic Encryption: Allows encrypted data processing
-
Zero-Trust Models: Restricts access and enforces strict authentication
Practical Tips
-
Encrypt full devices, not just files
-
Always keep backup copies of encrypted keys/passwords
-
Choose tools that match your technical skill level
-
Stay updated on threats and best practices
Final Thoughts
Encryption doesn’t have to be complicated. By using tools like BitLocker, VeraCrypt, or encrypted messaging apps, even beginners can take meaningful steps to protect their privacy and data. As threats grow and data moves to the cloud, encryption remains one of the strongest defenses you can use.
Popular articles



Comments (0)