

Ultimate Guide to Data Backup: Proven Strategies to Keep Your Files Safe
Introduction
Losing data—whether personal or professional—can have devastating consequences. From ransomware attacks to hardware failures, risks are everywhere. A strong data backup strategy ensures your critical files are protected, recoverable, and resilient against loss. This guide breaks down backup essentials, compares methods, and outlines how to safeguard your digital life or business operations.
Why Backups Are Essential
Backups are not optional—they’re your defense against data loss caused by:
-
Accidental deletion
-
System crashes
-
Cyberattacks and ransomware
-
Physical damage (fire, theft, floods)
The cost of data loss includes:
-
Financial losses from disrupted operations
-
Reputational damage
-
Time spent recreating lost data
-
Irreplaceable personal content
Backup Types Explained
-
Full Backup: A complete snapshot of data. Secure but time- and storage-heavy.
-
Incremental Backup: Backs up only changed files since the last backup. Efficient, but requires all backups in the chain.
-
Differential Backup: Backs up changes since the last full backup. Faster restoration than incremental.
Tip: Combine all three in your strategy—e.g., full backups weekly, incremental daily.
The 3-2-1 Backup Rule
The most widely recommended strategy:
-
3 total copies of data
-
2 types of media (e.g., SSD + cloud)
-
1 copy offsite
This approach protects against hardware failures, local disasters, and security breaches.
Local Backup Options
-
External HDD/SSD: Quick and private. Risks include theft or physical damage.
-
Network Attached Storage (NAS): Centralized, accessible by multiple users, can use RAID for redundancy.
-
Optical Discs (M-Disc): Useful for cold storage. Limited capacity and write speed.
Best Practice: Keep local backups secure and rotate them offsite regularly.
Cloud Backup Solutions
Popular services like Backblaze, iDrive, and Acronis offer:
-
Continuous or scheduled backups
-
Remote file access
-
Version control
-
Encryption and ransomware protection
Drawbacks:
-
Monthly/annual costs
-
Requires strong internet connectivity
Pro Tip: Use client-side encryption tools (e.g., Cryptomator) for added cloud security.
What Should You Back Up?
-
Full System Image: For fast recovery of your OS and apps
-
Critical Files Only: Essential docs, photos, projects
-
Hybrid Approach: System image monthly + daily incremental of key folders
Automating Backup Tasks
Avoid relying on memory—automate:
-
Windows: File History, System Image
-
macOS: Time Machine
-
Linux: Timeshift, Deja Dup
-
3rd Party Tools: EaseUS, Carbon Copy Cloner, BorgBackup
Set backup logs or email notifications to confirm completion.
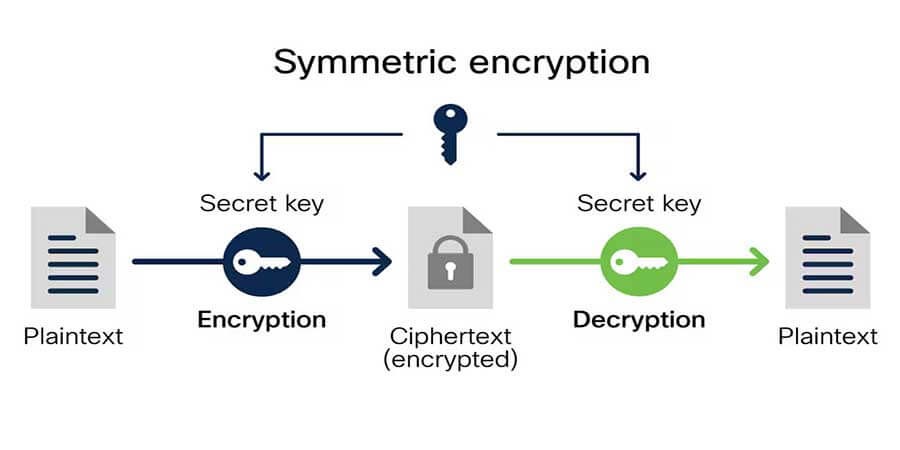
Encrypting Your Backups
Why encrypt?
-
Prevent unauthorized access
-
Meet compliance standards (HIPAA, GDPR, etc.)
Options:
-
BitLocker / FileVault: Full disk encryption
-
VeraCrypt: Encrypted containers
-
Zero-Knowledge Cloud: Sync.com, Tresorit
Enable two-factor authentication (2FA) on all backup-related accounts.
Version Control Systems (For Projects and Code)
Tools like Git, SVN, and Mercurial help track file changes:
-
Useful for coders, writers, and developers
-
Enables rollbacks, collaboration, and safe testing
Version control is ideal for frequently updated files, but not suitable for large binary files like video.
Offline, Online, and Offsite
Use a combination:
-
Offline (e.g., USB) to avoid hacking
-
Online (cloud) for instant access and automation
-
Offsite (external drive stored elsewhere) to protect from local disasters
For Businesses: Backup Policy Best Practices
-
Establish internal backup procedures
-
Use business-grade tools with logging and monitoring
-
Test restorations quarterly
-
Ensure encryption and access controls
-
Stay compliant with regulations (GDPR, HIPAA, PCI-DSS)
Common Mistakes to Avoid
-
Relying on one backup location
-
Skipping backup schedules
-
Forgetting encryption
-
Not verifying backup success
-
Ignoring application and OS settings in backup plans
Sample Backup Strategy
User: Freelance graphic designer
-
Daily: Auto-sync design files to Dropbox + Git for code
-
Weekly: Full system image to external SSD (BitLocker-enabled)
-
Monthly: Clone SSD to offline HDD stored offsite
-
Quarterly: Test file restoration
Result: Fast recovery possible from theft, malware, or system failure.
Emerging Trends
-
Snapshot Backups: ZFS, APFS allow precise state capture
-
Deduplication: Eliminate duplicate data blocks
-
Cold Cloud Storage: Low-cost long-term options (e.g., AWS Glacier)
-
Continuous Data Protection (CDP): Real-time file protection
-
AI & Ransomware Detection: Some tools detect suspicious patterns automatically
Final Thoughts
A proactive backup strategy shields your files from disasters, mistakes, and cyber threats. Use the 3-2-1 rule, automate wisely, and encrypt critical data. Whether you’re a home user or IT administrator, investing in robust backup habits today guarantees peace of mind tomorrow.
Popular articles


Comments (0)